This post was first published on: middle.
(t, n) Threshold Signature Scheme (TSS) is a cryptographic protocol that allows the following groups: N Participants jointly sign a document or transaction. tee + 1 More than one participant can produce a valid signature, but tea Or no less. The scheme is designed to enhance the security and trust of distributed systems by preventing unauthorized actions by ensuring that no single party can unilaterally generate signatures. TSS increases the security of encryption keys by dividing control between multiple parties. The key never exists.
Preliminary: Polynomial Interpolation
polynomial of degree (t-1) is uniquely determined by . tea points. For example, two points define a line and three points define a parabola.
If all points are scaled by a constant factor, the interpolated polynomial is also scaled by the same factor. The same goes for the y-intercept at x=0.
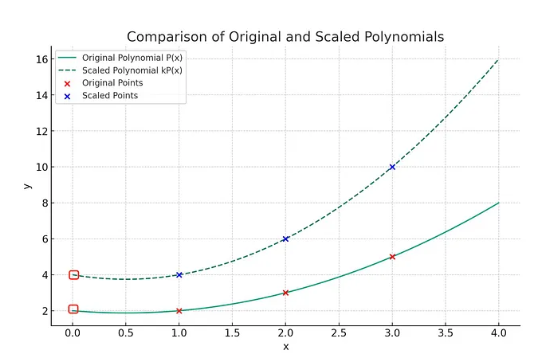
The example above has a polynomial. blood(X) is a quadratic that fits the points (1,2), (2,3), (3,5), and scaling the y values by 2 effectively scales them. blood(X) by 2 to get the interpolating polynomial for (1,4), (2,6), (3,10). The y-intercept is also adjusted by 2 from 2 to 4.
We will use this observation several times throughout the article.
Threshold signature scheme
Imagine a scenario where several groups are together. N Participants marked P₁ to Pₙ. In this setting, the (t, n) Threshold Signature Scheme (TSS) grants capabilities for all combinations of: tee + 1 Members jointly create signatures. However, groups less than or equal to tea The members lack this ability.
TSS includes three steps:
1. Generate key
As described in a previous post, the Distributed Key Generation (DKG) protocol is used.
Distributed key generation. The shared secret is your private key. skThis was not known to any party.
Assume that the DKG is run by participants, denoted P₁ to Pₙ, and each user Pᵢ receives an individual secret share. skᵢwith shared public key pk For verification purposes. skᵢ (T, N) Shamir Secret Sharing of Full Secrets sk. This key generation is a one-time initial setup step for TSS. This means that once established, private key sharing can be reused for multiple tasks.
shared public key pk This is the zero intercept of the contract interpolation method for all stocks (skᵢG) is broadcast during the Verifiable Secret Sharing (VSS) phase. To see why, check this out:
pk = skG
G at the generator point and is a constant. sk They all have 0 intercepts. skᵢof so pk That’s it? skᵢG‘S.
2. Create signature
Signature generation is performed in two steps.
- Generate partial signature: Each participant uses its share to generate a partial signature σᵢ. skᵢ In message M: σᵢ = S(skᵢM), S is the signature function.
- Partial signature aggregation: Aggregating these partial signatures produces the final signature, σ. The most important thing is to ensure that your private key never appears, so no secret leaks occur.
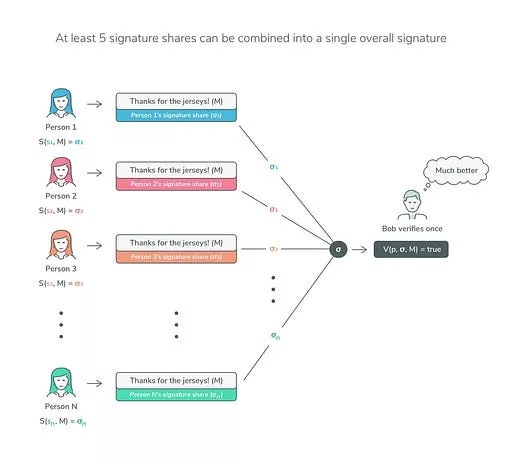

3. Signature verification
Verification of the threshold signature method is as follows. same This corresponds to a non-threshold counterpart. Anyone with access to the public key and message can verify the validity of the signature.
BLS Threshold Signature
There are several signature schemes that can be extended to threshold versions, including ECDSA, Schnorr, and BLS. We chose BLS as an example for ease of explanation.
key generation
After threshold key generation, each user Pᵢ gets a share of the key. skᵢand common public key pk For confirmation.
Create partial signature
These steps are identical to non-threshold BLS.
ᵢ creates a signature share as follows:
bloodᵢ = skᵢH(m)
middle It’s a message hour It is a cryptographic hash function.
Partial signature aggregation
The verifier first collects 𝑡diverse valid partial BLS signatures σᵢ from 𝑚.
The difficulty here is how to get σ from σᵢ without knowing it. sk.
σ = skH(m)
it turns out σ is the y-intercept of the Lagrange interpolation of all σ.ᵢ‘S.
This is because σᵢ is a constant factor of skᵢthat, H(m), shared by all participants. from sk is the y-intercept of all Lagrange interpolations. skᵢ‘In s DKG, σ is of all σᵢ.
check
The aggregate signature σ is now a valid signature for: middle For aggregate public keys pk. Signature verification is the same as the non-threshold version. The verifier checks the following equation:
e(H(m), pk) ?= e(σ, G)
pk is the aggregate public key and G This is the generator point.
comparison
Threshold Signatures combine DKG and MultiSig technologies, blending the best features of each. This convergence results in a powerful cryptographic solution that encapsulates the strengths of its predecessors.
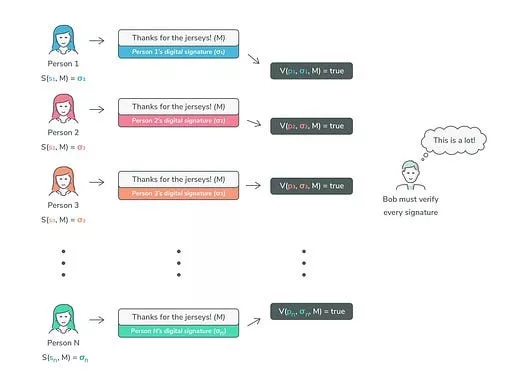
TSS vs. multisignature
Unlike multi-signature approaches, Threshold Signature Schemes (TSS) are known to produce more compact signatures while enhancing privacy protection. Additionally, TSS inherently extends multi-signature capabilities to blockchain technologies that do not directly support such capabilities, especially in situations where both efficiency and discretion are required. Crucially, The TSS architecture does not store private keys on the server., thereby strengthening risk management and promoting the sharing of responsibilities among participants. These outstanding advantages make TSS the optimal solution for developing secure hot wallets that operate in real time without compromising the confidentiality of private keys.

TSS vs DKG
In DKG, secrets can be created when a quorum of participants cooperate through sharing. In the context of signing, the secret is the private key. You can create it first and use it for signing. However, if the private key exists in its entirety, even briefly, it creates a single point of failure and makes it vulnerable to attack. In TSS, the private key does not exist and the private key is not visible in plaintext at any point in the signing process, making it immune to these attacks.
avatar
We implemented the (3, 5) threshold signature scheme in Bitcoin. Since ECDSA is natively supported in Bitcoin, we choose the ECDSA version of TSS. It is based on the tss-lib library.
A single execution results in the following transaction:
The address and signature will look identical to those generated normally without using TSS.
Watch: The sCrypt application is proving how powerful Bitcoin is.
Are you new to blockchain? To learn more about blockchain technology, check out CoinGeek’s Blockchain for Beginners section, our ultimate resource guide.


