
Welcome to the fascinating journey of unraveling the secrets behind Bitcoin, the cryptocurrency that has revolutionized the financial world. In this article, we will embark on a deep exploration of the origins, functioning, and impact of this digital innovation. We’ll delve into the complexities of blockchain technology, grasp the concept of bitcoin mining, and demystify security concerns. Get ready for an enlightening voyage as we uncover the universe of Bitcoin and decode the concepts that make this virtual currency so unique. This is your invitation to go beyond the surface and explore the opportunities and challenges that Bitcoin presents for the future of finance.

Breaking Barriers in Online Commerce
The way we conduct transactions on the internet is closely tied to financial institutions acting as trustworthy intermediaries for processing electronic payments. While this system works for most transactions, it still has inherent weaknesses in its trust-based model.
Imagine this: when disputes arise, financial institutions cannot entirely prevent intervention, making truly irreversible transactions challenging. This leads to higher mediation costs, restricting the practical minimum size of transactions and hindering casual small-scale transactions. The need for trust becomes a widespread concern, making merchants more cautious in their interactions with customers and accepting a certain percentage of fraud as unavoidable.
What we need is an electronic payment system based on cryptographic proof, eliminating the need for trust and enabling direct transactions between two parties. Transactions that are computationally impractical to reverse would protect sellers from fraud, while guarantee mechanisms could easily be implemented to safeguard buyers. An innovative solution to the double-spending problem involves using a distributed server of timestamps to generate computational proof of the chronological order of transactions.
The security of the system lies in its ability to prevent double spending when honest nodes collectively control more CPU processing power than any cooperative group of attacking nodes. This decentralized, cryptographic proof-based approach redefines trust in e-commerce, providing greater security and efficiency.
In simple terms, picture this as a secure and efficient way for people to buy and sell things online without worrying about fraud, thanks to a clever system that eliminates the need for blind trust. It’s like having a digital superhero protecting your online transactions!
Unraveling Bitcoin Transactions
In the realm of Bitcoin, an “electronic” currency is defined as a chain of digital signatures. The transfer of this currency happens when the current owner digitally signs a hash of the previous transaction, along with the public key of the next owner. These details are added to the end of the currency, creating a chain of ownership. The recipient can then verify the signatures to validate the ownership sequence.
However, a challenge arises in ensuring that one of the owners hasn’t spent the currency twice. The common solution would be to introduce a trusted central authority, or a mint, to verify each transaction for double spending. In this model, the currency must be returned to the mint after each transaction to issue new currency, and only coins directly issued by the mint are considered reliable against double spending.
Nevertheless, this centralized solution puts the fate of the entire monetary system in the hands of the company operating the mint. Every transaction must go through them, resembling the traditional banking model. The challenge is to create a method that allows the recipient to confirm that previous owners haven’t signed previous transactions without relying on a trusted entity.
In the Bitcoin model, the solution is the public disclosure of transactions. To prevent double spending without a trusted party, all transactions must be publicly announced, and a system is needed for participants to agree on a single history of the order in which they were received. The recipient needs proof that, at the time of each transaction, the majority of nodes agreed it was the first received.
Timing Transactions with Bitcoin
The solution proposed in the Bitcoin white paper begins with a crucial element: the Timestamp Server. This server plays a vital role in ensuring the chronological order of transactions, thereby establishing the integrity of the system.
The Timestamp Server operates by taking a hash of a block of items to be timestamped and widely publishing this hash, whether in a newspaper or a Usenet post. The timestamp proves that the data must have existed at that moment to be included in the hash. Each timestamp includes the previous timestamp in its hash, forming a chain where each additional timestamp reinforces the previous ones.
This chain of timestamps not only provides a reliable timestamp for transactions but also creates a structure that makes it extremely difficult to retroactively alter or falsify data. The inclusion of each timestamp in the hash of the next one creates an immutable connection between them, solidifying the order of transactions.
The widespread publication of hashes ensures transparency, as anyone can verify the authenticity and chronological order of transactions. There is no need to rely on a centralized entity to determine the sequence of events, making the system resistant to external manipulations.
In simple terms, think of this Timestamp Server as a trustworthy timekeeper for Bitcoin transactions, making sure everything happens in the right order and preventing any funny business with the data. It’s like having a digital notary to confirm when things happened and in what sequence!
Proof of Work in Bitcoin
To set up a distributed peer-to-peer timestamp server, Bitcoin adopts a proof-of-work system similar to Adam Back’s Hashcash, rather than relying on newspapers or Usenet posts. Proof of work is the key mechanism that strengthens security and trust in the system.
Proof of work involves searching for a value that, when hashed (e.g., with SHA-256), results in a hash starting with a specific number of zero bits. The average effort required is exponential in the number of required zero bits and can be verified by executing a single hash.
In Bitcoin’s timestamp network, proof of work is implemented by incrementing a nonce in the block until finding a value that provides the necessary zero bits in the block’s hash. Once CPU effort has been invested to satisfy the proof of work, the block cannot be changed without redoing the work. As later blocks are chained, altering one block would require redoing all subsequent blocks.
Proof of work also solves the problem of determining majority decision-making. While a majority based on one-IP-one-vote could be subverted by someone allocating many IPs, proof of work is essentially one-CPU-one-vote. Majority decision is represented by the longest chain, which has the greatest proof of work effort invested. If the majority of CPU power is controlled by honest nodes, the honest chain will grow faster and surpass any competing chains.
To modify a past block, an attacker would need to redo the proof of work for that block and all subsequent blocks, reaching and surpassing the work of honest nodes. The probability of a slower attacker catching up decreases exponentially as subsequent blocks are added.
To cope with increasing hardware speed and variations in interest to run nodes over time, the difficulty of proof of work is determined by a moving average targeting an average number of blocks per hour. If they are generated too quickly, the difficulty increases.

Bitcoin Network in Action
1. Broadcasting Transactions:
All recent transactions are broadcasted to every node in the network. This is the initial step to ensure that all transactions are known to the community.
2. Transaction Collection and Block Formation:
Each node gathers the new transactions and groups them into a block. This eases the processing and incorporation of transactions into the blockchain.
3. Proof of Work:
Every node begins the challenging task of finding a difficult proof of work for its block. This involves a trial-and-error process where nodes search for a specific value that meets hash requirements.
4. Block Transmission:
When a node finds a satisfactory proof of work, it broadcasts the block to all other nodes in the network. This signals the successful completion of the mining process.
5. Block Validation:
Nodes only accept the block if all transactions in it are valid and have not been spent. This validation is crucial to maintain the integrity of the blockchain.
6. Chain Extension:
Nodes demonstrate their acceptance of the block by working on creating the next block in the chain. The hash of the accepted block becomes the previous hash of the next block, forming a continuous sequence.
7. Consensus on the Longest Chain:
Nodes always consider the longest chain as the correct one and continue working to extend it. If two nodes transmit different versions of the next block simultaneously, some nodes may receive one before the other. In this case, they work on the one they received first but keep the other on standby in case it becomes longer.
8. Final Decision:
The final decision is made when the next proof of work is found, and one of the branches becomes longer. Nodes that were working on the other branch then switch to the longer one.
9. Network Tolerance:
Broadcasting new transactions doesn’t need to reach every node. As long as it reaches many nodes, transactions will be included in a block soon. Block transmission also tolerates lost messages. If a node doesn’t receive a block, it will request it when receiving the next block and realizing it missed one.

Incentivizing Integrity
Traditionally, the first transaction in a block is special, marking the beginning of a new currency owned by the creator of the block. This practice not only provides an incentive for nodes to support the network but also establishes an initial means of distributing coins in circulation, without relying on a central authority to issue them.
The constant addition of new coins is akin to gold miners investing resources to introduce gold into circulation. In the context of Bitcoin, CPU time and electricity are expended to create new coins. This practice not only boosts the security and integrity of the network but also provides a rewarding mechanism for participants.
The initial reward can be complemented with transaction fees. If the output value of a transaction is less than its input value, the difference becomes a transaction fee added to the block reward value containing the transaction. After a predetermined number of coins enter circulation, the reward can transition entirely to transaction fees, becoming completely inflation-free.
Incentives play a crucial role in promoting the honesty of nodes. If a greedy attacker manages to gather more CPU power than all honest nodes combined, they have to choose between using it to defraud people by stealing their payments or using it to generate new coins. It is more profitable for them to play by the rules, favoring them with more new coins than all others combined, than to undermine the system and compromise the validity of their own wealth.

Optimizing Disk Space
Once the latest transaction in a coin is buried under enough blocks, spent transactions before it can be discarded to save disk space. To do this without compromising the block’s hash, transactions are grouped into a Merkle Tree, and only the root is included in the block’s hash.
Older blocks can be compressed by trimming branches of the tree. Inner hashes don’t need to be stored, allowing for a significant reduction in space occupied by older blocks.
A block header without transactions would be around 80 bytes. Assuming blocks are generated every 10 minutes, 80 bytes * 6 * 24 * 365 = 4.2MB per year. With computers typically sold with 2GB of RAM in 2008 and Moore’s Law predicting a current growth of 1.2GB per year, storage shouldn’t be an issue, even if block headers need to be kept in memory.
In simpler terms, think of this like cleaning up your computer files. Once a transaction is securely stored in enough blocks, we can tidy up the details, saving space without jeopardizing the security of the network. It’s like organizing your computer folders — keeping only what’s essential, so things run smoothly and efficiently.

Simplified Payment Verification in Bitcoin
You can verify payments without running a full node on the network. A user only needs to maintain a copy of the block headers from the chain with the longest proof of work. This can be obtained by querying network nodes until the user is convinced they have the longest chain. Additionally, the user can get the Merkle branch linking the transaction to the block in which it’s timestamped.
While the user can’t verify the transaction themselves, by linking it to a spot in the chain, they can see that a node on the network accepted it. Subsequently added blocks further confirm that the network accepted it.
Verification is reliable as long as honest nodes control the network but becomes more vulnerable if the network is dominated by an attacker. While network nodes can verify transactions themselves, the simplified method can be fooled by transactions fabricated by an attacker, as long as the attacker can keep outpacing the network.
A strategy to guard against this would be to accept alerts from network nodes when they detect an invalid block. This would prompt the user’s software to download the complete block and alerted transactions to confirm the inconsistency. Companies receiving frequent payments would likely still want to run their own nodes for more independent security and quicker verification.

Privacy in Bitcoin
The traditional banking model achieves a level of privacy by limiting access to information to only the involved parties and a trusted third party. The need to publicly announce all transactions hinders this method, but privacy can still be maintained by disrupting the flow of information elsewhere: keeping public keys anonymous.
Transactions in Bitcoin can be viewed by the public, indicating that someone is sending an amount to someone else, but without information linking the transaction to any individual. This is similar to the level of information disclosed by stock exchanges, where the time and size of individual trades, known as the “tape,” are public, but the involved parties are not revealed.
To reinforce privacy, a new key pair should be used for each transaction, avoiding linkage to a common owner. Some linkage is still unavoidable with multi-input transactions, which reveal that their inputs were owned by the same owner. The risk is that if the owner of one key is revealed, the linkage could expose other transactions owned by the same individual.
In transactions with multiple inputs, revealing that their inputs were owned by the same owner poses challenges to maintaining complete anonymity. The disclosure of the owner of a key could potentially expose other transactions linked to that owner.

Attack and Defense Strategies in Bitcoin
Let’s explore a scenario where an attacker is trying to generate an alternative chain faster than the honest chain. Even if achieved, this doesn’t open the system to arbitrary changes, such as creating value out of thin air or taking money that never belonged to the attacker. Nodes won’t accept an invalid transaction as payment, and honest nodes will never accept a block containing them. The attacker can only attempt to change one of their own transactions to reclaim money spent recently.
The race between the honest chain and an attacker’s chain can be characterized as a Binomial Random Walk. The success event is the honest chain being extended by one block, increasing its lead by +1, and the failure event is the attacker’s chain being extended by one block, reducing the difference by -1.
The probability of an attacker reaching breakeven from a given deficit is analogous to a Gambler’s Ruin problem. The probability of an attacker never reaching breakeven or never reaching the honest chain can be calculated.
The expression for the probability of an attacker reaching the honest chain is given by the following equation:
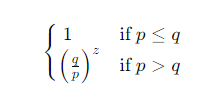
Under the assumption that p > q , the probability decreases exponentially as the number of blocks the attacker needs to catch up increases. If the attacker doesn’t make significant progress early on, their chances become practically nil as they fall further behind.
The recipient of a new transaction needs to wait long enough before being sure that the sender can’t alter the transaction. The calculation involves the probability of the attacker succeeding in reaching the honest chain, taking into account the time and the number of blocks added after the transaction.
Bitcoin: A Trustless System for Electronic Transactions
We introduce a trustless system for electronic transactions. Starting with the conventional structure of coins created from digital signatures, which provides strong ownership control but lacks a way to prevent double-spending.
To address this issue, we propose a peer-to-peer network using proof of work to record a public transaction history that quickly becomes computationally impractical for an attacker to alter if honest nodes control the majority of CPU processing power. The network is robust in its unstructured simplicity. Nodes work simultaneously with little coordination, need not be identified, and messages are not routed to any specific location. Nodes can freely join and exit the network, accepting the proof-of-work chain as evidence of what happened while they were absent. They vote with their CPU processing power, expressing acceptance of valid blocks by working to extend them and rejecting invalid blocks by refusing to work on them. Any necessary rules or incentives can be enforced with this consensus mechanism.
The proposal provides an effective solution to the double-spending problem, ensuring robust and secure transparency in electronic transactions. The simplicity of the peer-to-peer network, combined with proof of work, creates a reliable system where honest nodes are incentivized to maintain network integrity. The flexibility of the consensus mechanism allows the application of rules and incentives, adapting to ever-evolving needs. Bitcoin emerges as an innovative milestone in the quest for decentralized and secure financial systems.
Bitcoin stands out as an exciting proposition to democratize online transactions, eliminating the need to trust financial institutions. By leveraging blockchain technology and proof of work, Bitcoin offers a secure and decentralized approach to the double-spending problem. In summary, the future of electronic transactions may be closer than we imagine.
LinkedIn: felipe-rainel
Email: raineldias88@gmail.com
Unraveling Bitcoin: A Journey Towards Understanding Cryptocurrencies was originally published in Coinmonks on Medium, where people are continuing the conversation by highlighting and responding to this story.

